Phishing is a common type of cyber-attack where attackers attempt to acquire sensitive information from people such as bank details or passwords, often by pretending to be an organisation that the victim trusts. It’s important to be aware of the various methods of phishing and how to protect yourself from them.
With three billion – yep, 3,000,000,000 – phishing emails sent every day, accounting for 1% of all email traffic, this type of cyber-attack is not one that any organisation should be brushing under the carpet. Everyone should be aware of the different types of phishing, not just email phishing, and how to stay alert to the efforts of cyber criminals.
Kit Barker, Chief Information Security Officer at Agilio, says: “Despite all the technical defences organisations have in place, people falling victim to simple phishing attacks remains one of the main ways cyber-criminals breach those defences. It is crucial that we all understand how to spot the fake emails from the real ones. This article will help you understand the various forms of phishing so you have a better chance of not becoming a victim.”
Below are a few examples of how cyber criminals may attempt a phishing attack.
Quishing – When cyber-criminals use malicious QR codes
QR codes have become increasingly popular in advertising and marketing in recent years, mainly because they offer an extremely convenient way to help consumers reach a particular piece of content – all we have to do is scan with our phones! However, QR codes do obscure the destination URL – we often can’t see the URL it’s leading to until we’ve scanned the code – and this is why they have become popular amongst phishers too!
Phishers may send you an email, for example, posing as a clothing brand that you’re a regular customer of, and the email may include a QR code encouraging you to scan to see their new clothing line. But these cyber-criminals create malicious QR codes that aim to direct victims to unsafe websites.
So, to protect yourself from dangerous QR codes, be wary when scanning any that come from untrusted sources. And even if it seems trustworthy, for example if you are sent an email asking you to scan a QR code to reset a password, if you weren’t expecting this email then it could be malicious. You could find an app or a particular QR code scanner that gives you a preview of the URL before opening, so you get a chance to check if it looks a safe and reliable link before you go to the content.
Email phishing – The most traditional type of phishing
Phishers are very partial to using email as a route of attack; it’s a classic but effective phishing tactic. A phishing email can pose a risk from various angles; the cyber-criminal behind the sneaky email could disguise themselves as an organisation you trust in order to lure you in.
This type of phishing attack often includes a link asking you to do something, such as ‘re-verify your account’, asking you to enter your login details. This is because phishers are on the hunt for sensitive information like bank details or login credentials.
If you do receive emails of this fashion, the best thing to do is login the way you usually do and check if there’s a message in there about re-verifying, or whatever the email was asking you to do. Otherwise, contact the organisation directly through their official channels, and ask if the email is legitimate.
Smishing – When phishers target you via mobile
This is another common type of phishing, known as ‘smishing’, coming from ‘SMS phishing’. This route of attack involves cyber-criminals sending you text messages that include malicious links or other prompts, again, often disguised as an organisation you trust.
As with any type of phishing, and smishing is no different, these messages may contain very urgent wording. A smishing text may be posing as a message from your bank, warning you that there’s an issue with your account and you need to log in immediately. Such messages, exploiting human psychology, aim to panic people into clicking on a malicious link in the SMS message, which they are led to think is a safe link to log into their online banking.
Recognise a legitimate myhrtoolkit email
Below, you can see the email address that you will commonly receive myhrtoolkit emails from, for example, a holiday request approval email - alert@mg.myhrtoolkit.com.
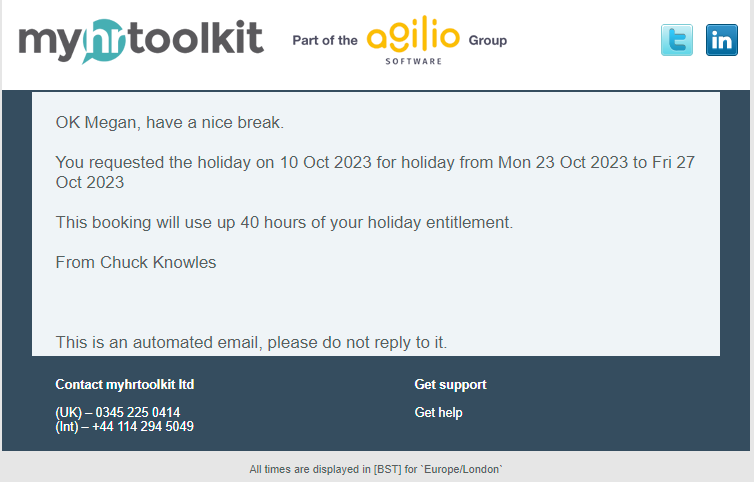
The image below shows what a holiday request approval email will look like. Note that there are no QR codes, links, or anything asking you to login.
You’re in safe hands with myhrtoolkit
At myhrtoolkit, we take phishing – and cybersecurity as a whole – extremely seriously. If you ever receive an unexpected email from us, or any other type of communication that you’re unsure about, don’t click on the links until you’re sure it’s safe. Instead, login via the app.
And of course, you can always give us a call to ask if something is legitimate or not, we’re happy to help anytime!

Written by James Lawson
James is a marketing executive at myhrtoolkit, and he's responsible for engaging the company’s existing customer and partner base on digital channels and creating helpful resources targeted at HR professionals and business managers.

 Holiday Planner
Holiday Planner Absence Management
Absence Management Performance Management
Performance Management Staff Management
Staff Management Document Management
Document Management Reporting
Reporting Health and Safety Management
Health and Safety Management Task Management
Task Management Security Centre
Security Centre Self Service
Self Service Mobile
Mobile



